0x01 本地化集成包更新服务
安装集成更新服务
容器
docker pull docker.elastic.co/package-registry/distribution:8.15.3
这个包很大, 建议使用🪜安装
启动
docker run -it -p 8080:8080 docker.elastic.co/package-registry/distribution:8.15.3使用该方式,每次有更新的时候,都需要重新拉取新包,比较麻烦, 后面会讲到使用程序进行自动更新
自编译
如果想要Kibana不去es官网而是从我们内网环境中获取集成组件的相关数据,就需要使用es官网提供的package-registry服务
相关源代码如下: https://github.com/elastic/package-registry
基础环境准备
系统环境中需要安装golang, 目前的版本要求是1.23版本
wget https://go.dev/dl/go1.23.2.linux-amd64.tar.gz 编译更新服务
wget https://github.com/elastic/package-registry/archive/refs/tags/v1.26.0.zip
unzip v1.26.0.zip
cd package-registry-1.26.0
go build修改配置文件
config.yml
package_path参数根据具体环境指定即可,这里我将该路径指定为可执行程序的当前目录的packages目录下
package_paths:
- ./packages
cache_time.index: 10s
cache_time.search: 10m
cache_time.categories: 10m
cache_time.catch_all: 10m启动服务
./package-registry --address 0.0.0.0:8080同步集成包
获取所有的集成包信息
https://epr.elastic.co/search
如果加上get参数all=true,https://epr.elastic.co/search?all=true则表示获取所有的包。没有参数默认只返回最新的包。
返回格式如下:
[
{
"name": "1password",
"title": "1Password",
"version": "1.10.0",
"release": "ga",
"description": "Collect logs from 1Password with Elastic Agent.",
"type": "integration",
"download": "/epr/1password/1password-1.10.0.zip",
"path": "/package/1password/1.10.0",
"icons": [
{
"src": "/img/1password-logo-light-bg.svg",
"path": "/package/1password/1.10.0/img/1password-logo-light-bg.svg",
"title": "1Password",
"size": "116x116",
"type": "image/svg+xml"
}
],
"policy_templates": [
{
"name": "1password",
"title": "1Password Events",
"description": "Collect events from 1Password Events Reporting"
}
],
"conditions": {
"kibana": {
"version": "^8.6.1"
}
},
"owner": {
"github": "elastic/security-external-integrations"
},
"categories": [
"security",
"credential_management"
],
"signature_path": "/epr/1password/1password-1.10.0.zip.sig"
},
.....
]然后根据上面的返回的数据,从url
https://package-storage.elastic.co/artifacts/packages/进行下载,比如下载1password,根据上面获取的数据中的signature_path字段,下载
# 下载安装包
https://package-storage.elastic.co/artifacts/packages/1password-1.10.0.zip
#下载hash
https://package-storage.elastic.co/artifacts/packages/1password-1.10.0.zip.sig实现自动化的集成更新程序。
package main
import (
"encoding/json"
"fmt"
"io"
"log"
"net/http"
"os"
"path/filepath"
"strings"
"time"
)
type UpdateIntegrations struct {
installedIntegrations map[string]bool
allIntegrations map[string]bool
interval time.Duration
directory string
newIntegrationsCount int
}
func NewUpdateIntegrations(directory string, interval time.Duration) *UpdateIntegrations {
return &UpdateIntegrations{
installedIntegrations: make(map[string]bool),
allIntegrations: make(map[string]bool),
interval: interval,
directory: directory,
}
}
var integrationClient = &http.Client{
Transport: &http.Transport{DisableKeepAlives: false},
}
func (ui *UpdateIntegrations) getAllIntegrationsInfo() {
log.Println("Getting all integrations info")
client := &http.Client{}
//"https://epr.elastic.co/search?all=true") # 获取所有的包
req, err := http.NewRequest("GET", "https://epr.elastic.co/search", nil)
if err != nil {
log.Fatalf("Failed to create request: %v", err)
}
req.Header.Set("User-Agent", "Kibana/8.15.3 node-fetch")
resp, err := client.Do(req)
if err != nil {
log.Fatalf("Failed to get response: %v", err)
}
defer resp.Body.Close()
var items []map[string]interface{}
if err := json.NewDecoder(resp.Body).Decode(&items); err != nil {
log.Printf("Failed to decode JSON: %v", err)
}
for _, item := range items {
if signaturePath, ok := item["signature_path"].(string); ok {
filename := strings.TrimSuffix(filepath.Base(signaturePath), ".sig")
ui.allIntegrations[filename] = true
} else {
log.Printf("Get signature_path error: %v", item["name"])
}
}
log.Println("getAllIntegrationsInfo success")
}
func (ui *UpdateIntegrations) downloadFile(url, filename string) error {
req, err := http.NewRequest("GET", url, nil)
if err != nil {
return fmt.Errorf("failed to create request: %w", err)
}
req.Header.Set("User-Agent", "Kibana/8.15.3 node-fetch")
resp, err := integrationClient.Do(req)
if err != nil {
return fmt.Errorf("failed to get response: %w", err)
}
defer resp.Body.Close()
out, err := os.Create(filepath.Join(ui.directory, filename))
if err != nil {
return fmt.Errorf("failed to create file: %w", err)
}
defer out.Close()
_, err = io.Copy(out, resp.Body)
if err != nil {
return fmt.Errorf("failed to write to file: %w", err)
}
return nil
}
func (ui *UpdateIntegrations) downloadIntegrations(filename string) {
for i := 0; i < 3; i++ {
if i > 0 {
log.Printf("Download integrations failed, retry %d", i)
}
url := fmt.Sprintf("https://package-storage.elastic.co/artifacts/packages/%s", filename)
if err := ui.downloadFile(url, filename); err != nil {
log.Printf("Download integrations error: %v", err)
time.Sleep(2 * time.Second)
continue
}
sigFilename := filename + ".sig"
sigURL := fmt.Sprintf("https://package-storage.elastic.co/artifacts/packages/%s", sigFilename)
if err := ui.downloadFile(sigURL, sigFilename); err != nil {
log.Printf("Download integrations sig file error: %v", err)
time.Sleep(2 * time.Second)
continue
}
ui.newIntegrationsCount++
log.Printf("Download new integrations success: %s", filename)
return
}
}
func (ui *UpdateIntegrations) readPackagesName() {
files, err := os.ReadDir(ui.directory)
if err != nil {
log.Fatalf("Failed to read directory: %v", err)
}
for _, file := range files {
if strings.HasSuffix(file.Name(), ".sig") {
ui.installedIntegrations[strings.TrimSuffix(file.Name(), ".sig")] = true
}
}
}
func (ui *UpdateIntegrations) updateIntegrations() {
for {
ui.getAllIntegrationsInfo()
ui.readPackagesName()
for filename := range ui.allIntegrations {
if !ui.installedIntegrations[filename] {
ui.downloadIntegrations(filename)
}
}
log.Printf("updateIntegrations done, install new package number: %d", ui.newIntegrationsCount)
log.Printf("sleep %f seconds", ui.interval.Seconds())
ui.newIntegrationsCount = 0
time.Sleep(ui.interval)
}
}
func main() {
logFile, err := os.OpenFile("./update_integrations.log", os.O_APPEND|os.O_CREATE|os.O_WRONLY, 0644)
if err != nil {
log.Fatalf("Failed to open log file: %v", err)
}
defer logFile.Close()
log.SetOutput(logFile)
log.Println("update_integrations start")
updateIntegrations := NewUpdateIntegrations("./packages", 24*time.Hour)
updateIntegrations.updateIntegrations()
}
配置kibana
修改kibana的配置文件/etc/kibana/kibana.yml ,让其默认访问我们搭建的内网集成服务
xpack.fleet.isAirGapped: true
xpack.fleet.registryUrl: "http://127.0.0.1:8080"重启kibana服务,完成
systemctl restart kibana0x02 本地化二进制包升级服务
官网的地址为:https://artifacts.elastic.co
下载所有的二进制包
curl -O https://artifacts.elastic.co/downloads/apm-server/apm-server-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/apm-server/apm-server-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/apm-server/apm-server-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/beats/auditbeat/auditbeat-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/beats/auditbeat/auditbeat-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/beats/auditbeat/auditbeat-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/beats/elastic-agent/elastic-agent-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/beats/elastic-agent/elastic-agent-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/beats/elastic-agent/elastic-agent-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/beats/heartbeat/heartbeat-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/beats/heartbeat/heartbeat-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/beats/heartbeat/heartbeat-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/beats/metricbeat/metricbeat-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/beats/metricbeat/metricbeat-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/beats/metricbeat/metricbeat-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/beats/osquerybeat/osquerybeat-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/beats/osquerybeat/osquerybeat-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/beats/osquerybeat/osquerybeat-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/beats/packetbeat/packetbeat-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/beats/packetbeat/packetbeat-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/beats/packetbeat/packetbeat-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/cloudbeat/cloudbeat-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/cloudbeat/cloudbeat-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/cloudbeat/cloudbeat-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/endpoint-dev/endpoint-security-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/endpoint-dev/endpoint-security-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/endpoint-dev/endpoint-security-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/fleet-server/fleet-server-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/fleet-server/fleet-server-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/fleet-server/fleet-server-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-host-agent-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-host-agent-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-host-agent-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-elastic-collector-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-elastic-collector-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-elastic-collector-8.15.3-linux-x86_64.tar.gz.asc
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-elastic-symbolizer-8.15.3-linux-x86_64.tar.gz
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-elastic-symbolizer-8.15.3-linux-x86_64.tar.gz.sha512
curl -O https://artifacts.elastic.co/downloads/prodfiler/pf-elastic-symbolizer-8.15.3-linux-x86_64.tar.gz.asc然后自己搭建一个文件服务器即可完成。
注意: 访问的链接的格式建议满足 http[s]:/[你的域名或者IP+端口]/downloads/beats/osquerybeat/osquerybeat-8.15.3-linux-x86_64.tar.gz.sha512
最后在fleet-》设置 里面设置即可
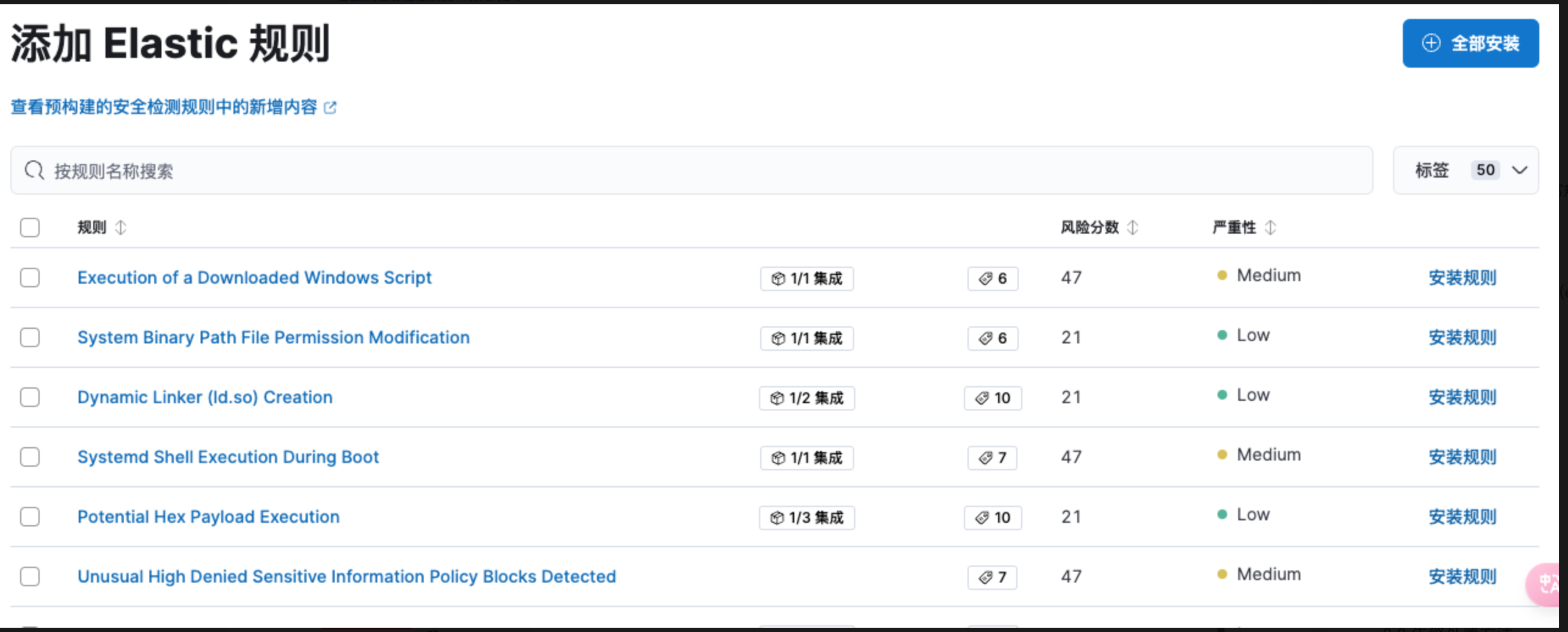
0x03 规则更新
3.1 客户端规则更新(endpoint规则)
默认情况下,endpoint 通过自动从https://artifacts.security.elastic.co 下载客户端安全检测规则来持续防御最新的威胁,由于当前使用版本以及网络延迟问题,需要设置本地规则服务器用于客户端规则更新。
整体流程如下:
1)下载当前正在使用的endpoint 版本的规则,以当前使用的版本8.15.3为例:
export ENDPOINT_VERSION=8.15.3 && wget -P downloads/endpoint/manifest https://artifacts.security.elastic.co/downloads/endpoint/manifest/artifacts-$ENDPOINT_VERSION.zip && zcat -q downloads/endpoint/manifest/artifacts-$ENDPOINT_VERSION.zip | jq -r '.artifacts | to_entries[] | .value.relative_url' | xargs -I@ curl "https://artifacts.security.elastic.co@" --create-dirs -o ".@"执行上述命令后,本地规则文件将下载到:downloads/endpoint/manifest/artifacts-8.15.3.zip,文件下载完成后,对文件进行解压获取manifest.json,文件内容片段如下:
"diagnostic-configuration-v1": {
"compression_algorithm": "zlib",
"decoded_sha256": "a3d6ed843b4ff6abe466d20e310472381ebc9a5958355df19ab544a5322f6cac",
"decoded_size": 8527,
"encoded_sha256": "b94cc4b1c2632d49cfe8cbf105bab77e9922f1e77a38cf0b29b59b998a87fd80",
"encoded_size": 1264,
"encryption_algorithm": "RC4-c51f5065b860947796aeff228ebe409c",
"relative_url": "/downloads/endpoint/diagnostic-configuration-v1/b94cc4b1c2632d49cfe8cbf105bab77e9922f1e77a38cf0b29b59b998a87fd80"
},将manifest.json 文件放到和endpoint-rule规则批量下载工具一个文件夹下,然后执行endpoint-rules程序。
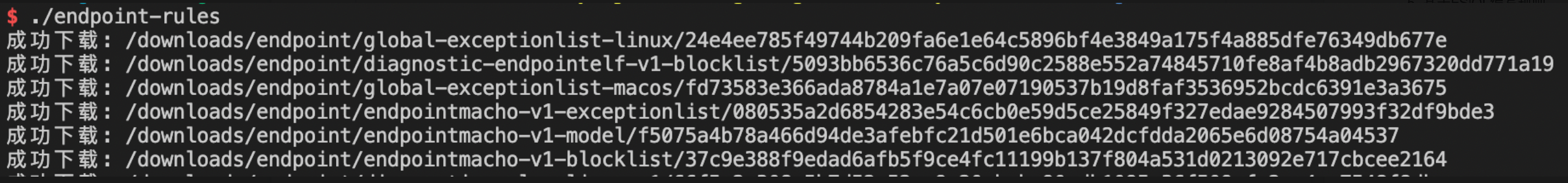
成功后,文件会下载到当前目录下的download 目录:
downloads
└── endpoint
├── diagnostic-configuration-v1
│ └── b94cc4b1c2632d49cfe8cbf105bab77e9922f1e77a38cf0b29b59b998a87fd80
├── diagnostic-endpointelf-v1-blocklist
│ └── 5093bb6536c76a5c6d90c2588e552a74845710fe8af4b8adb2967320dd771a19
├── diagnostic-endpointelf-v1-exceptionlist
│ └── 30aeab4ad131ea70bd21e9c2e9528b4d178279aa3c8fe6de57c5645e49a185a9
├── diagnostic-endpointelf-v1-model
│ └── 98611a30e1ce18f374d6e3d81934581f475cf644cf56434120915de660ca6a6b
├── diagnostic-endpointmacho-v1-blocklist
│ └── 5e0cbcbcc1b63c0b89a85c80b1a7622d29d1d5cd94a4738e5fd21d61fc823758
├── diagnostic-endpointmacho-v1-exceptionlist
│ └── 2c1331ad1667fbc57f81e202a9dcdfe1eb6c9a06897721f0e465ba238794f12c
├── diagnostic-endpointmacho-v1-model
│ └── 3549f309cd96f9f3203897b89cc95200741a2adb8d08efbdaf97f3200c7c64b6
├── diagnostic-endpointpe-v4-blocklist
│ └── 02ffbee79a29413f8479aa0e3106acd2a5aa5cad366364da1ea30b59125d8667
├── diagnostic-endpointpe-v4-exceptionlist
│ └── c4eed6af530782b68b11cad0a702b51149832ec9a9dbbdce857c5ac5cf8f7f83
├── diagnostic-endpointpe-v4-model
│ └── ad6aea96cc1ba0e1a24efb01540aef6d6d6c40f342f99bb6052c559ebfae9d4d
├── diagnostic-malware-signature-v1-linux
│ └── 8b5da9e6baf3407b01692123f0986245fbd25db3395a5310e5438ef8d5dad88b
├── diagnostic-malware-signature-v1-macos
│ └── 5b9b73ad8368ac51d313d01ee8b4edcbca2e3e722056ee5c6924cd5231200206
├── diagnostic-malware-signature-v1-windows
│ └── b9490a5eba6e44356544cca165cd7e0c0645ae99ab268d535a29ae39cd879ecd
├── diagnostic-ransomware-v1-windows
│ └── 2bb3efd0d907b3575039b227d341f6cf132398a764d0adb0d3b94c45152f9574
├── diagnostic-rules-linux-v1
│ └── 66f5a2e308c5b7d52c52cc9c20ebcbe90cdb1095c36f509afc2ca4ea7548f8db
├── diagnostic-rules-macos-v1
│ └── c9ea6b22410c45aaab61e27f63f50897bf19dff7dede86dc58aec42f5935dcf5
├── diagnostic-rules-windows-v1
│ └── 450c74e7f94d0b6dc15551f863f4d5a6b037508e15886015dc70af3c79bfe734
├── endpointelf-v1-blocklist
│ └── ac2d9422b1b393944685126590282d9a801bf8150187f723408a3d51e368bc2d
├── endpointelf-v1-exceptionlist
│ └── 277de851fee8bb4e612bcaaf1f155518936d633567dd8c0a209ea131ba634f45
├── endpointelf-v1-model
│ └── ca945fb4b8e2eb3a768d5600449805df173ca757e803f6030c848396484ac2f2
├── endpointmacho-v1-blocklist
│ └── 37c9e388f9edad6afb5f9ce4fc11199b137f804a531d0213092e717cbcee2164
├── endpointmacho-v1-exceptionlist
│ └── 080535a2d6854283e54c6cb0e59d5ce25849f327edae9284507993f32df9bde3
├── endpointmacho-v1-model
│ └── f5075a4b78a466d94de3afebfc21d501e6bca042dcfdda2065e6d08754a04537
├── endpointpe-v4-blocklist
│ └── 78a7ece75189e5a7e299a7e275c9f6e59f0d0f11741c336013c1972b644bf968
├── endpointpe-v4-exceptionlist
│ └── b7cdfcff408dfe4033970eaef33b8c82021ec152204ffeb08b9aceff21c75377
├── endpointpe-v4-model
│ └── be76eea284ea7ba74eb05d1f4ce9d50983d98b3998705cedc8c7e926c8d9bc0e
├── global-configuration-v1
│ └── cec6f83704a5ffda6718ee50fd4fc0a573c616a22f7ba7a1fdfa20dae10e7448
├── global-eventfilterlist-linux-v1
│ └── 48ae9c16f4be1ebfdf7fb223d2661dc8bb5c37a0d391c93dd820a3e4e1691102
├── global-eventfilterlist-macos-v1
│ └── 41b31c0a4f153459ec1a34e89210055ed2a72c6aab65adedff849a408b36dd8b
├── global-eventfilterlist-windows-v1
│ └── c183d685507e4df192286f6bde50f59573025b703d1263d1e5ce3cb5d9cfa890
├── global-exceptionlist-linux
│ └── 24e4ee785f49744b209fa6e1e64c5896bf4e3849a175f4a885dfe76349db677e
├── global-exceptionlist-macos
│ └── fd73583e366ada8784a1e7a07e07190537b19d8faf3536952bcdc6391e3a3675
├── global-exceptionlist-windows
│ └── 3e4e384e9a131c1a788b67ed9654282ed7e4acc22436d8aeccfa2ed361e84874
├── global-trustlist-linux-v1
│ └── d593c090ed8cc805e0a5b281312c4c6f71c42db7d166fd813788438164d0d5b3
├── global-trustlist-macos-v1
│ └── 96786deb6191f7664d0598473c9f453f3b11fc972656f27bbebe604e7e339b7f
├── global-trustlist-windows-v1
│ └── ca99c72828da451526f7d3d624de5659c72a2f43434feff64bf28ba64a3d7c6d
├── production-malware-signature-v1-linux
│ └── 2b0f53235fc2a7b5fc988c4254f6289650ba87fd70780fb5969ea2d1e12bc78b
├── production-malware-signature-v1-macos
│ └── a0001e04d9a58b7a20a3b92cf0d1d5921506ab8ec48454d6cb7c64eeafe23684
├── production-malware-signature-v1-windows
│ └── 3df1f36fd64d09a53180cff515965c0263b565c7134c0f29fef9aabcd19d9c88
├── production-ransomware-v1-windows
│ └── 86f9c2a2446c3c9bdc0c53bbba82970316243edbbcff361e646fdb53a54a0855
├── production-rules-linux-v1
│ └── f53bb44c5410bd72656d22cf3813ad8b4f7144edb012f97320619cdc24aea546
├── production-rules-macos-v1
│ └── f86db753522798f8aee95a1907e5f0ecdfbb3adeddaf4c6766671d76b4fd1c90
├── production-rules-windows-v1
│ └── 57256e880dba2116b8b28af97332a9ba8bb9e5969ca9775bcd6451c095f41de8
├── ransomware-v1-artifact-windows
│ └── 0aaa2c3e420b2aa4e72bbb8ee9942fe52094bc0b9ff0924544cfac4a288de216
└── tamper-protection-config-v1
└── bdc4f41615a708fbabaf29e7aca660f71321bf3ef9f2f263079bb372f0de13032)上传规则到本地更新服务器
本地更新服务器地址为 http://static.sec.tech ,登录该服务器上传刚刚下载的文件到/data/wwwroot/es_artifacts 目录下对应的目录中。
默认已在平台上策略中配置了endpoint 规则更新地址为 http://static.sec.tech,如启用新的配置,需要设置endpoint 高级策略中的本地规则下载地址参数linux.advanced.artifacts.global.base_url、mac.advanced.artifacts.global.base_url、windows.advanced.artifacts.global.base_url的值为http://static.sec.tech。
3.2 服务端规则更新
单条规则更新
规则错误问题更新规则:
自定义规则:直接在XDR V2 平台上对相应的自定义规则进行更新。
开源规则:按照规则版本横向方法进行更新。
规则版本更新:
导出规则:打开需要规则版本更新的规则详情页面,点击右上角的操作按钮,选择导出规则。
更新规则:规则导出为ndjson扩展名的文件,直接在规则文件上对规则进行更新,同时修改版本。
导入规则:在规则管理界面点击导入规则,上传刚刚修改完的文件,勾选覆盖具有冲突rule_id、list_id、id
删除规则:关闭并删除老版本规则
另外需要注意的是,新创建的规则需要再规则名称后增加(JJSEC) 标志,自定义规则需要写明作者。
开源规则更新
获取本地规则集版:在部署kibana的主机上打开
/usr/local/kibana/node_modules/@kbn/fleet-plugin/target/bundled_packages/目录,查看本地规则集security_detection_engine-x.x.x.zip的版本,例如获取到本地规则集版本为8.15.6获取最新规则集版本:请求远程es 规则更新API(
https://epr.elastic.co/search?package=security_detection_engine&kibana.version=8.15.3)获取当前最新的规则集版本,获取到最新规则集版本为8.15.17。下载最新的规则集:根据返回的下载地址或者使用url拼接下载地址(
https://epr.elastic.co/epr/security_detection_engine/security_detection_engine-8.15.17.zip),获取最新的规则集安装包。更新规则集:将规则集安装包放到
/usr/local/kibana/node_modules/@kbn/fleet-plugin/target/bundled_packages/目录下后,重启kibana服务,就可以显示最新版本规则集的更新规则和新增规则了。