场景
使用suricata做网络入侵检测的告警,zeek做网络流量的深度分析
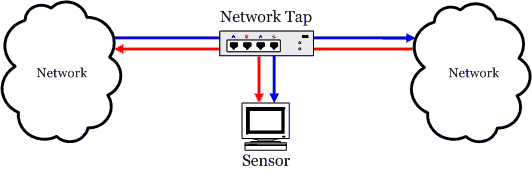
接入到sensor的上下行分开的两路流量, 需要有两个网卡进行采集,但是这有出现了一个问题, zeek对两个网卡的上下行流量嗅探组包比较困难。 目前我使用的方式是网卡bond,通过将两张网卡组成一个bond,让zeek直接在bond虚拟网卡进行抓包。
安装
bond配置
配置步骤如下(针对centos 7)
- 新建bond虚拟网卡
# 创建配置文件
touch /etc/sysconfig/network-scripts/ifcfg-bond010
# 配置网卡
DEVICE="bond010"
ONBOOT=yes
USERCTL=no
BONDING_OPTS="mode=0 miimon=100"
BOOTPROTO=none
- 修改监听网卡的配置
# 修改p1p2网卡
TYPE=Ethernet
NAME="p2p1"
DEVICE=p2p1
ONBOOT=yes
MASTER="bond010"
SLAVE=yes
# 修改p1p2网卡
TYPE=Ethernet
NAME="p2p2"
DEVICE=p2p2
ONBOOT=yes
MASTER="bond010"
SLAVE=yes
- 重启网卡服务器
systemctl restart network
- bond网卡开启混杂模式
ifconfig bond010 promisc
ifconfig p2p1 promisc
ifconfig p2p2 promisc
- 查看当前bond状态
cat /proc/net/bonding/bond5
Ethernet Channel Bonding Driver: v3.7.1 (April 27, 2011)
Bonding Mode: load balancing (round-robin)
MII Status: up
MII Polling Interval (ms): 100
Up Delay (ms): 0
Down Delay (ms): 0
Slave Interface: p2p1
MII Status: up
Speed: 10000 Mbps
Duplex: full
Link Failure Count: 0
Permanent HW addr: b4:96:91:1b:64:b4
Slave queue ID: 0
Slave Interface: p2p2
MII Status: up
Speed: 10000 Mbps
Duplex: full
Link Failure Count: 0
Permanent HW addr: b4:96:91:1b:64:b6
Slave queue ID: 0
suricata配置
安装
开启上下行流量抓包
suricata其实是支持上下行流量组包检测的,只需要修改suricata的配置文件即可
基于af-packet的tap模式
# Linux high speed capture support
af-packet:
- interface: p2p2
# Number of receive threads. "auto" uses the number of cores
threads: auto
#cluster-type: cluster_qm
# Default clusterid. AF_PACKET will load balance packets based on flow.
cluster-id: 99
# Default AF_PACKET cluster type. AF_PACKET can load balance per flow or per hash.
# This is only supported for Linux kernel > 3.1
# possible value are:
# * cluster_flow: all packets of a given flow are sent to the same socket
# * cluster_cpu: all packets treated in kernel by a CPU are sent to the same socket
# * cluster_qm: all packets linked by network card to a RSS queue are sent to the same
# socket. Requires at least Linux 3.14.
# * cluster_ebpf: eBPF file load balancing. See doc/userguide/capture-hardware/ebpf-xdp.rst for
# more info.
# Recommended modes are cluster_flow on most boxes and cluster_cpu or cluster_qm on system
# with capture card using RSS (requires cpu affinity tuning and system IRQ tuning)
cluster-type: cluster_flow
# In some fragmentation cases, the hash can not be computed. If "defrag" is set
# to yes, the kernel will do the needed defragmentation before sending the packets.
defrag: yes
# To use the ring feature of AF_PACKET, set 'use-mmap' to yes
use-mmap: yes
# Lock memory map to avoid it being swapped. Be careful that over
# subscribing could lock your system
#mmap-locked: yes
# Use tpacket_v3 capture mode, only active if use-mmap is true
# Don't use it in IPS or TAP mode as it causes severe latency
#tpacket-v3: yes
# Ring size will be computed with respect to "max-pending-packets" and number
# of threads. You can set manually the ring size in number of packets by setting
# the following value. If you are using flow "cluster-type" and have really network
# intensive single-flow you may want to set the "ring-size" independently of the number
# of threads:
#ring-size: 2048
# Block size is used by tpacket_v3 only. It should set to a value high enough to contain
# a decent number of packets. Size is in bytes so please consider your MTU. It should be
# a power of 2 and it must be multiple of page size (usually 4096).
#block-size: 32768
# tpacket_v3 block timeout: an open block is passed to userspace if it is not
# filled after block-timeout milliseconds.
#block-timeout: 10
# On busy systems, set it to yes to help recover from a packet drop
# phase. This will result in some packets (at max a ring flush) not being inspected.
#use-emergency-flush: yes
# recv buffer size, increased value could improve performance
# buffer-size: 32768
# Set to yes to disable promiscuous mode
# disable-promisc: no
# Choose checksum verification mode for the interface. At the moment
# of the capture, some packets may have an invalid checksum due to
# the checksum computation being offloaded to the network card.
# Possible values are:
# - kernel: use indication sent by kernel for each packet (default)
# - yes: checksum validation is forced
# - no: checksum validation is disabled
# - auto: Suricata uses a statistical approach to detect when
# checksum off-loading is used.
# Warning: 'capture.checksum-validation' must be set to yes to have any validation
#checksum-checks: kernel
# BPF filter to apply to this interface. The pcap filter syntax applies here.
#bpf-filter: port 80 or udp
# You can use the following variables to activate AF_PACKET tap or IPS mode.
# If copy-mode is set to ips or tap, the traffic coming to the current
# interface will be copied to the copy-iface interface. If 'tap' is set, the
# copy is complete. If 'ips' is set, the packet matching a 'drop' action
# will not be copied.
uffer-size: 64535
- interface: p2p1 # 监听下行流量接口
threads: auto # 自动分配线程
cluster-id: 100 # 为第二个接口指定一个不同的集群 ID
cluster-type: cluster_flow # 仍按照流规则分发
zeek安装
安装
- 安装基础环境
sudo yum install cmake make gcc gcc-c++ flex bison libpcap-devel openssl-devel python3 python3-devel swig zlib-devel
使用devtoolset安装cmake3
yum install -y centos-release-scl
sudo yum install cmake3 devtoolset-7
scl enable devtoolset-7 bash
- 安装可选项依赖
pip3 install GitPython semantic-version
# 或者
sudo yum install python3-GitPython python3-semantic_version
- 下载zeek
wget <https://download.zeek.org/zeek-4.0.9.tar.gz>
tar zvxf zeek-4.0.9.tar.gz
cd zeek-4.0.9
./configure --with-pcap=/usr/local/lib
make -j 24 && make install
安装插件
插件地址 : Zeek Package Manager: Packages
安装插件,需要外网,gcc版本需要大于7
./zkg install zeek/corelight/zeek-community-id
zeek/corelight/zeek-community-id : zeek是必须的, corelight表示制作者, zeek-community-id表示插件名称
安装完成后,重新运行 ./zeekctl deploy即可在日志文件 conn.log中看见community_id:
{
"ts": 1677493871.186421,
"uid": "CnYHdB2pqY3xg4GWgg",
"id.orig_h": "192.168.130.12",
"id.orig_p": 47296,
"id.resp_h": "52.25.176.52",
"id.resp_p": 443,
"proto": "tcp",
"duration": 2.0040030479431152,
"orig_bytes": 0,
"resp_bytes": 0,
"conn_state": "S0",
"local_orig": true,
"local_resp": false,
"missed_bytes": 0,
"history": "S",
"orig_pkts": 2,
"orig_ip_bytes": 96,
"resp_pkts": 0,
"resp_ip_bytes": 0,
"community_id": "1:R9UbzFVXprFpdRFb79v214yT9v4="
}
日志关联
基于conn.log中uid进行关联,比如 uid=CcaCXW2grRyJgVX0yg。这可以在http.log找到该uid对应的详细日子
{
"ts": 1677494094.371831,
"uid": "CcaCXW2grRyJgVX0yg",
"id.orig_h": "192.168.34.13",
"id.orig_p": 50028,
"id.resp_h": "182.50.10.149",
"id.resp_p": 80,
"trans_depth": 1,
"method": "POST",
"host": "extshort.weixin.qq.com",
"uri": "/mmtls/5817452a",
"version": "1.1",
"user_agent": "MicroMessenger Client",
"request_body_len": 803,
"response_body_len": 33022,
"status_code": 200,
"status_msg": "OK",
"tags": [],
"orig_fuids": [
"FTDJce3j1AZVgX3jOd"
],
"resp_fuids": [
"FDTEbK3TaSD9FlMGGd"
]
}
其他
升级cmake
wget <https://cmake.org/files/v3.16/cmake-3.16.3.tar.gz> # <https://cmake.org/files/> 自己选版本
tar zvxf cmake-3.16.3.tar.gz
cd cmake-3.16.3
./bootstrap --prefix=/usr/local
make -j 12
make install
cmake --version